Securing Sensitive Data with Secrets
We copied a feature straight from GitHub! Sorry, GitHub!
Chipper CI now supports secrets. These are sort of like environment variables, except they're encrypted.
You can create secrets on your Teams and on each Project.
Secrets saved to a Team are available in every build for each project in that team.
Secrets you create in a Project over-ride secrets created in the Team if they have the same name.
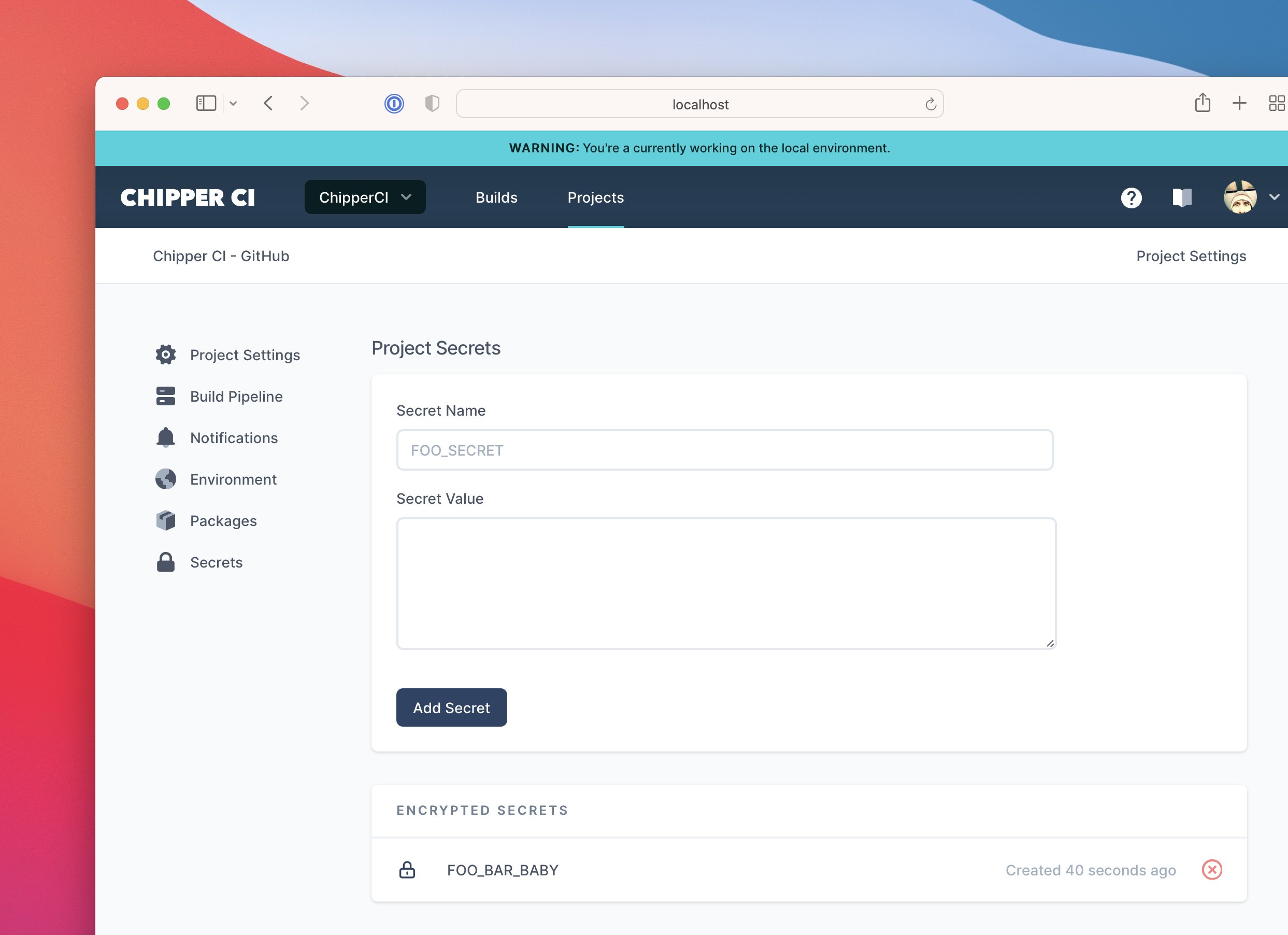
How does it work?
In our search for how to best implement Secrets in Chipper CI, we came across this GitHub page.
That sounded awesome, but we weren't sure how it encrypted stuff client-side!
Well, we promptly went to GitHub's form for creating a Secret, hacked GitHub opened up the network inspector, and clicked some buttons. It turns out, we can see that it uses the NPM package Tweetsodium.
Finding that, we set to work. What we do is generate a key pair per project and team. When creating a secret, we pass the public key to javascript. When a secret is created, javascript uses that public key encrypt the secret value.
The encrypted value is then sent to our servers. We only see the encrypted value!
Using Secrets
We can decrypt the secret with the private key, which we keep stored securely.
Within your builds, Secrets are just plain old environment variables. You can use them as usual:
# Maybe for API keys!
curl -H "Authorization: $SOME_SECRET_API_KEY" https://example.org/do/something/cool
# Maybe for deployments!
echo -n $MY_SECRET_KEY > ~/.ssh/id_deploy
chmod 0600 ~/.ssh/id_deploy
ssh -i ~/.ssh/id_deploy user@example.org /opt/start_deploy.sh
Keeping secrets secret
We do our best to redact secrets from build output. This was actually hard! For example,sometimes newline characters are removed from long, multi-line secrets. We've written a bunch of code to help there - just in case!
If you do something silly like echo $MY_EXTREMELY_IMPORTANT_SECRET as a build step, Chipper should be able to remove it from the build output. We redact it before buid output reaches our storage.

